How to log into the container registry
Preparations
Before you can use the DTZ container registry, you need to enable the service first.
- Enable the service
- Access the container registry dashboard
- Container Registry Dashboard
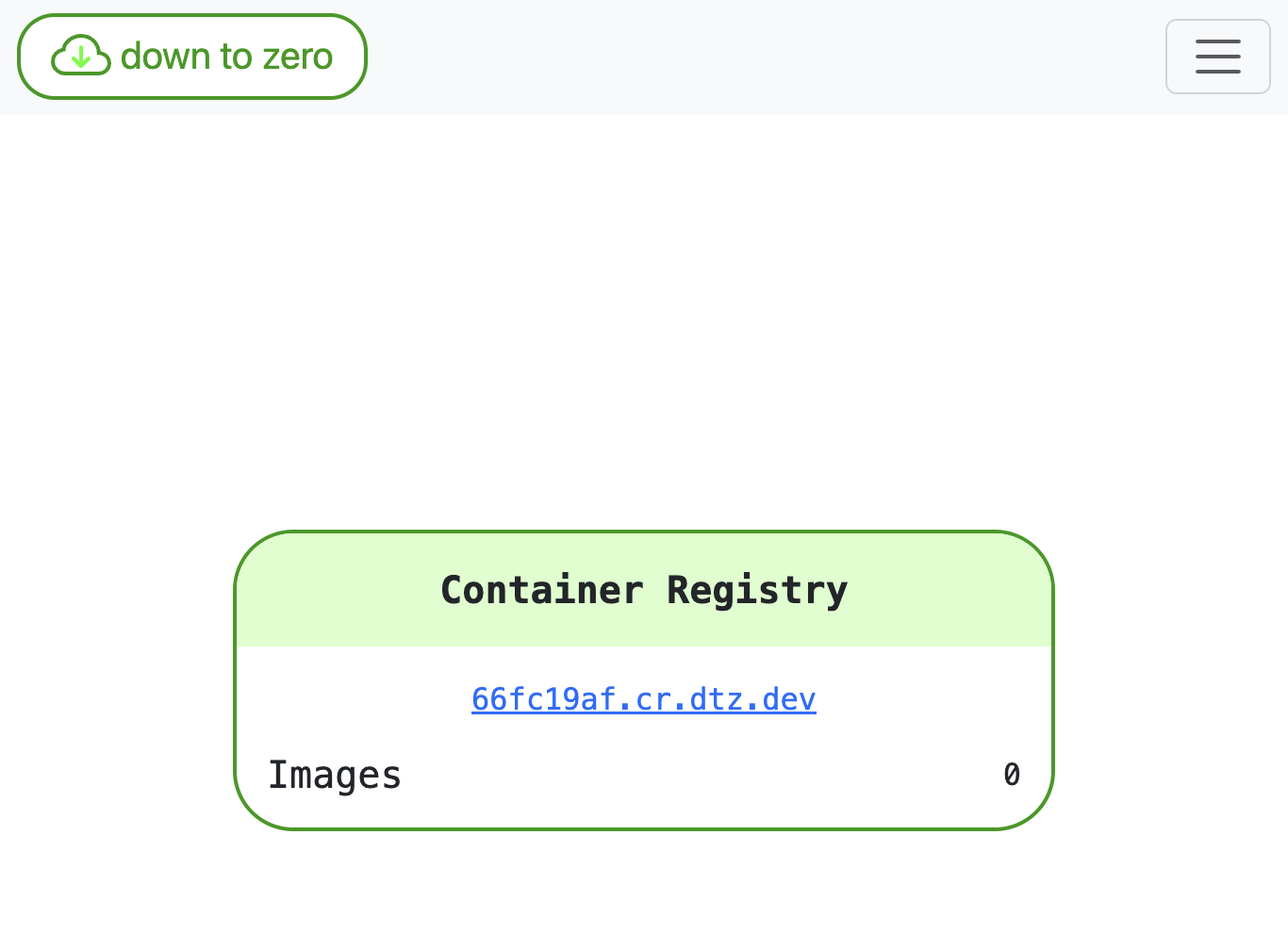
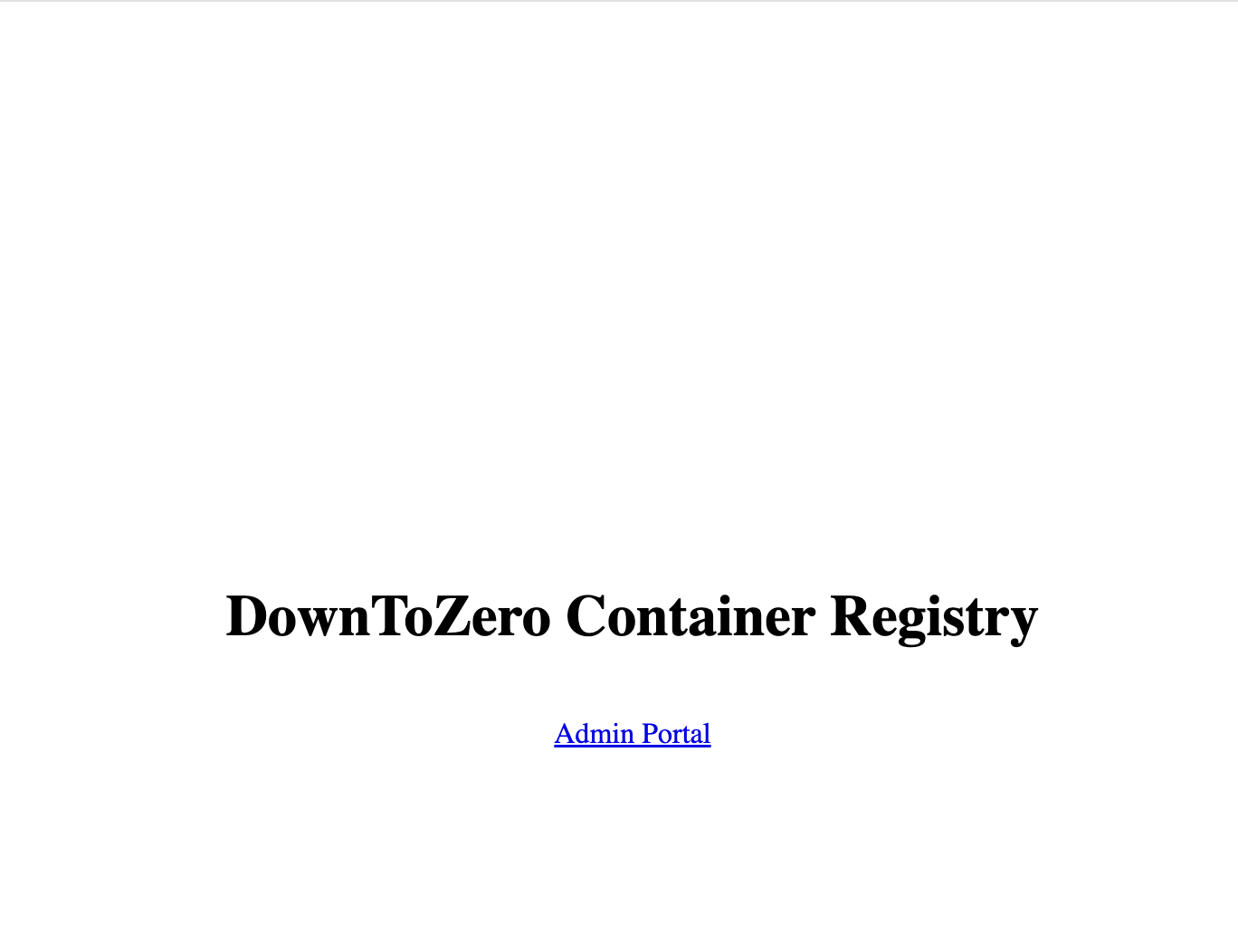
- Testing the registry endpoint
You can click the link on the dashboard to test your registry instance. This link should lead you to the following page.
After completing the setup, you need to retrieve your instance URL from the container registry dashboard, in this case, https://66fc19af.cr.dtz.dev/.
So all images are hosted under 66fc19af.cr.dtz.dev.
Docker Login
The easiest way to login is via API-key. You can following the guide in our docs on how to create an API-key.
To perform the login you can use the terminal:
docker login 66fc19af.cr.dtz.dev
Username: apikey
Password: {past in you API-key here}
Login Succeeded
This registers you credential in the docker daemon and you can now push and pull images to that registry.
Kubernetes Credentials
In kubernetes, managing credential cannot be handled by interacting the docker daemon directly. Therefore you need to provide credentials via the deployment definitions as secret.
If you have access to kubectl, you can following the instruction from the official documentation.
kubectl create secret docker-registry <name> \
--docker-server=DOCKER_REGISTRY_SERVER \
--docker-username=DOCKER_USER \
--docker-password=DOCKER_PASSWORD \
--docker-email=DOCKER_EMAIL
Often times, kubectl access is not an option, since all deployments run through some CI/CD system which needs you to provide the secret as YAML. So here are the steps to take to manually create such a secret.
- base64 encode your credentials
echo 'DOCKER_USER:DOCKER_PASSWORD' | base64
RE9DS0VSX1VTRVI6RE9DS0VSX1BBU1NXT1JECg==
- place the credential string into a docker config json, and store this as
credentials.json.
{
"auths": {
"66fc19af.cr.dtz.dev": {
"auth": "RE9DS0VSX1VTRVI6RE9DS0VSX1BBU1NXT1JECg=="
}
}
}
- base64 encode the whole file
cat credentials.json | base64
ewogICAgImF1dGhzIjogewogICAgICAgICI2NmZjMTlhZi5jci5kdHouZGV2IjogewogICAgICAgICAgICAiYXV0aCI6ICJSRTlEUzBWU1gxVlRSVkk2UkU5RFMwVlNYMUJCVTFOWFQxSkVDZz09IgogICAgICAgIH0KICAgIH0KfQo=
- create a Secret with the encoded credential file inside.
apiVersion: v1
kind: Secret
type: kubernetes.io/dockerconfigjson
metadata:
name: dtz-credentials
data:
.dockerconfigjson: ewogICAgImF1dGhzIjogewogICAgICAgICI2NmZjMTlhZi5jci5kdHouZGV2IjogewogICAgICAgICAgICAiYXV0aCI6ICJSRTlEUzBWU1gxVlRSVkk2UkU5RFMwVlNYMUJCVTFOWFQxSkVDZz09IgogICAgICAgIH0KICAgIH0KfQo=
- after applying this secret to you kubernetes cluster, you can use private images.
apiVersion: v1
kind: Pod
metadata:
name: private-ubuntu
spec:
containers:
- name: private-ubuntu-container
image: 66fc19af.cr.dtz.dev/ubuntu
imagePullSecrets:
- name: dtz-credentials